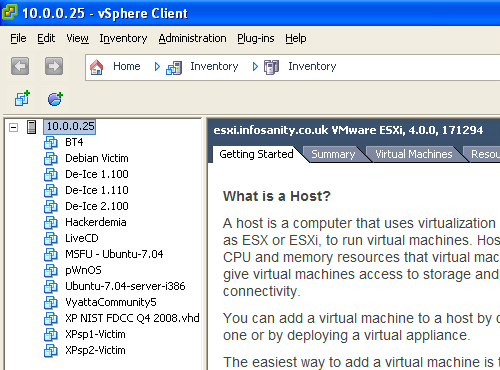
The previous post on lab machines seemed to generate a high level of interest so I thought it may be worthwhile to expand further and share my lab’s network setup.
My recent exploration of the Vyatta platform’s capabilities has provided a simple method for segregating and connecting lab networks without requiring a hardware router. I currently split my network into three seperate subnets.
- 10.0.0.0/24 – Physical network for none virtual machines
- 192.168.1.0/24 – Primary lab subnet
- 192.168.2.0/24 – Secondary lab subnet
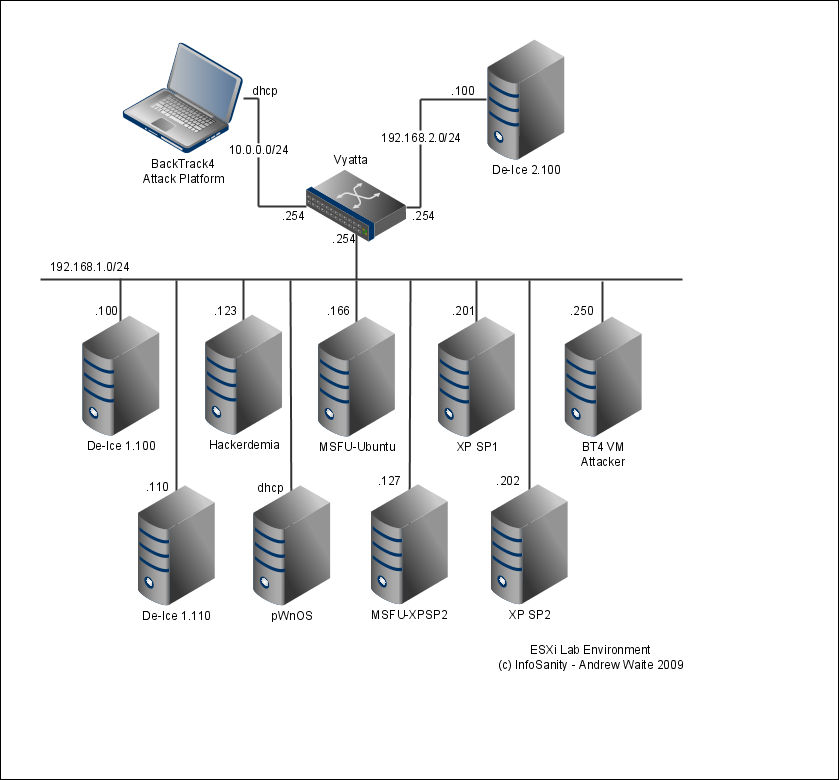
The primary lab subnet contains the majority of my victims. Helpfully the machines configured as part of Metasploit Unleashed and most of the machines released by Heorot.net (De-ICE level1 and Hackerdemia) both use the 192.168.1.0/24 subnet. To fit I’ve configured my custom machines to match. While providing additional targets, the custom machines in the primary lab double as my malware analysis environment (with the Vyatta appliance powered off to provide isolation).
My secondary lab subnet currently only contains the single publically available level 2 De-ICE machine. In the future I’m intending to expand the usage of the secondary lab by dual-homing one or more of the of the lab machines and demoing pivot and techniques to use one a compromised machine to attack otherwise inaccessible targets.
With the machines and environment detailed above and in the previous post I’ve managed to develop a highly versatile lab environment for both tool/exploit development and training/practice. Not bad for a total outlay of under £200 plus some time and effort.
— Andrew Waite