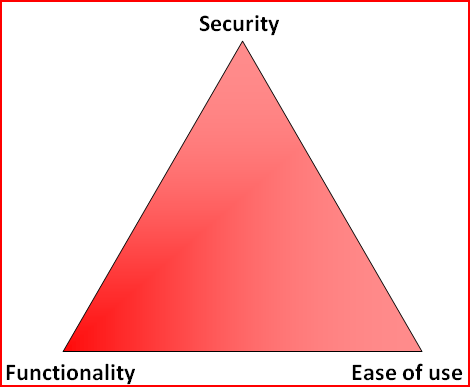
Following from an introduction of the C.I.A. Triangle another triangle is used to help explain the relationship between the concepts of security, functionality and ease of use. The use of a triangle is because an increase or decrease in any one of the factors will have an impact on the presence of the other two.
As an example, increasing the amount of functionality in an application will also increase the surface area that a malicious user can attack when attempting to find an exploitable weakness.
The trade-off between security and ease of use is commonly encountered in the real world, and often causes friction between users and those responsible for maintaining security. Microsoft had long been targetted by the security community for allowing everyday users to operate the system with administrative or system level permissions, which resulted in any exploit targeting a userland application was immediately given access with full rights. When Microsoft tried to limit this functionality by forcing users to specifically request elevated privilages via User Access Control (UAC) there were high number of complaints from users who weren’t happy with the extra actions required to complete tasks. As a result many instructions and guides were created to teach users how to disable the UAC functionality; increasing the ease with use and decreasing the steps needed to perform some tasks, but at the expense of disabling an improved security system.
A recent blog post discussing the security of windows operating system states, quite colorfully that:
Leaving the bias and hyperbole of the above, rightly or wrongly developers are able to write to the filesystem, registry and hook API calls in order to provide the functionality expected and requested by end users. From this standpoint no functional operating system will never be 100% secure, what every system and ultimately user must settle on a compromise between acceptable functionality and usability, and acceptable security.
–Andrew
<Update>:
I’d been looking for this Dilbert strip when writing the post, just came across it now, enoy:

</update>
Very true Andrew, users and organizations are indeed trying to find a balance between security, functionality and ease of use.
Here is something I would like you to think about…
If you could start over again from scratch, and re-engineer all the hardware, software and applications – and how everything interacts with each other; how could you achieve the same functionality and ease of use, yet have everything significantly more secure than it is today? Think about how systems, applications and data can be compromised; and how to prevent a hacker from injecting code or taking control of a system. It’s not an easy exercise for sure, but try it.
Is it possible to make a system 100% secure starting from scratch? Perhaps not, but I bet if you could get pretty close. 😉
Cheers
This is a tough tradeoff but I would much rather be secure and have something a little tougher to use than to have my information unsecured.
I would agree; for my own systems I like UAC and leave enabled, don’t really see a difference between it and ‘nix’s su/sudo. Likewise my flashdrives and sensitive documents are TrueCrypt containers. This all requires a couple of extra steps when working occassionally but I had seen no noticable impact to my productivity since shifting to more secure working methods.
But I fear that you (and anyone else inclinded to visit this site) and I aren’t representative of the general populous. If we were systems and networks would be more secure and we’d quite likely be out of a job ;).