As promised when the postman delivered the Alfa equipment, I’ve done some initial analysis of my first wireless capture. The data being analysed was collected during the evening commute back home, a trip that includes urban, sub-urban and rural areas so should be good representative sample group.
Security
The previous wireless post has already touched on the security aspect of the found access points. The chart below shows the breakdown between the the various security implementations. The WPA+ category includes WPA, WPA2 and WPA2WPA columns (as categorised by airodump-ng).
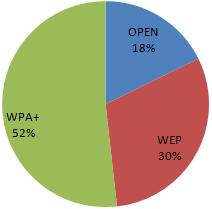 Due to the known insecurities within WEP, almost half of the encountered access points do not have any reliable security in place to protect the attached network and users of their networks.
Due to the known insecurities within WEP, almost half of the encountered access points do not have any reliable security in place to protect the attached network and users of their networks.
Default Configurations
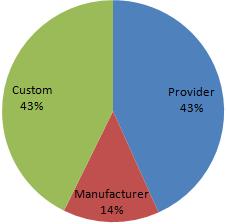
Most, potentially all wireless access points have the ability to be configured in a secure manner. However, a large percentage home and small office users are not aware of the security implications of wireless equipment or other computer technology. As a result the default factory settings that a wireless device is shipped with often provides the baseline security configuration. The below diagram shows that over 50% of the encountered access points were running in a default state (either provider or manufacturer settings) [n.b. assumption is based solely on essid]
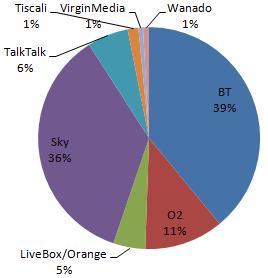
The issue is shown by the split of the BT Home Hub devices, BT are one of the major telecommunications providers within the UK. The initial Home Hub (with default ESSID of BTHomeHub-####) are, in this data set, exclusively protected by WEP. In contrast the majority of newer versions of the same device (ESSID: BTHomeHub2-####) operate with the WPA/WPA2 protocols. Another large UK telecoms player, SKY appears to take security of their provided devices seriously all encountered access points configured with SKY’s default ESSID (SKY#####) almost exclusively employ WPA. The chart below shows the provider breakdown of the encountered access points (obviously we are unable to determine the provider of access points with a custom ESSID), with the dominance of BT and Sky in this area the default configuration of their devices could be crucial for a large number of home users.
Custom ESSIDs
Whilst some default configurations are insecure, some modified configurations may inadvertently provide additional information to potential attackers. One advantage behind default configurations is that it can be difficult to determine the location or physical connections of any given access point, however the ESSID can provide a good probability of determining the physical connections. Numerous access points within the data have ESSIDs set to an address or individuals name, this is potentially unavoidable for businesses. Whilst security through obscurity can never replace solid security, some obscurity and misdirection can reduce risk and volume of compromise attempts. As a prime example, this data set includes an access point related (assuming ESSID is relevant) of a local branch of a national bank, more worryingly the access point appears to be running WEP.
A large volume of modified ESSIDs are given ‘humorous’ values or references to pop-culture. Some network names may be references/retorts from the network owners in response finding unauthorised users on the network, Dont-steal-our-network and we-know-who-u-are-thief. Both these networks run WPA2, potentially learning the security message the hard way.
The last network name that caught attention may be an attempt at offensive security, the ESSID reboot may potentially be an attempt to trip up malicious users parsing available networks through poorly considered shell script.
Summary
Within the dataset analysed the findings show that wireless infrastructure is becoming widespread. Further to this, the volume of default and insecure configurations may indicate that the usage and security implications of wireless connectivity may not be well understood within the general population. The growing trend of wireless enabled devices to be shipped with secure default configurations is a positive move within this field.
— Andrew Waite
Leave a comment
With the bank running WEP, usually the same VPN type access used to secure internet access to an internal network is used with wireless connections as well… usually.