As the world (or at least, myself) begins to emerge from Lockdown, in-person events are returning. For me, this was initiated with an excellent trip to Manchester, experiencing Matillion’s Super All Hands gathering, meeting with new colleagues that had until that point merely been faces on a collage of Zoom tiles. As part of the […]
Category archives: Honeypot
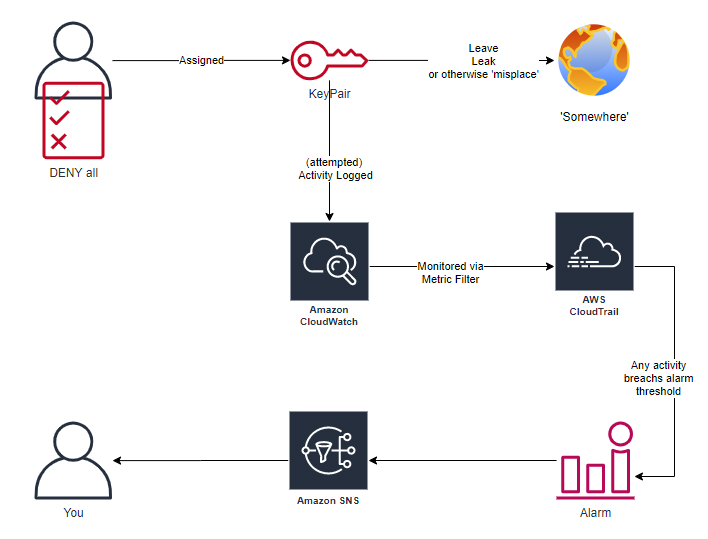
AWS HoneyUsers
Deception technology and techniques are having a resurgence, expanding beyond the ‘traditional’ high/low- interaction honeypots, into honeyfiles, honeytokens and (as you may have guessed from title) honeyusers. Today is the culmination of a “what if?” idea I’d been thinking for years, actually started working on earlier in the year (but then 2020 happened), but is […]
Cowrie SSH Honeypot – AWS EC2 build script
Happy New Year all! Whilst eating FAR too much turkey and chocolates over the festive break, I’ve managed to progress a couple of personal projects on (between stints on the kids’ Scalectrix track, thanks Santa). Still tasks to do(*), but a working EC2 User-Data script to build to automate deployment Cowrie honeypot has reached MVP […]
Tales from the Honeypot: Bitcoin miner
My Kippo farm has been largely retired as most of the captured sessions where becoming stale and ‘samey’. Thankfully however, I’ve still been getting daily reports thanks to this script (now available in BitBucket repo) and this morning something new caught my attention – a ‘guest’ attempted to turn the compromised machine into a BitCoin miner.
Pipal password analysis of Kippo password useage
Trying to find an opportunity to give Pipal a run out, I decided to take a look at the passwords gathered by my Kippo installation. First up, I decided to take a look at the passwords used with added accounts once intruders compromise the system. Curious to see if the passwords chosen by those that break systems are vulnerable to the same weaknesses of standard users.
HoneyD network architecture
I was recently asked about the network configuration I use for my honeyd sensor. As I now have a pretty(ish) network diagram showing my setup as a result, decided sharing is caring.
Starting with Artillery
announced the alpha release of a new honeypot, Artillery.
Artillery is a combination of a honeypot, file monitoring and integrity, alerting, and brute force prevention tool. It’s extremely light weight, has multiple different methods for detecting specific attacks and eventually will also notify you of insecure nix configurations.
Kippo – Clearing pass.db
Very quick post to highlight a process for clearing all entries from your pass.db file.
Kippo – pass.db
After a few weeks running my daily Kippo review script I’ve noticed that whilst I’m still mostly receiving several logins per day, it’s rare for a connection to actually interact with my emulated system. So I started trying to investigate what was causing the trend.
Reviewing Kippo Logs
When I first started running Kippo almost a year ago I had no difficulty getting motivated to log into the honeypot, check for new connections and generally get a feel for what my victims visitors have been up to. Slowly I’d check the logs less frequently, so I built a quick script to provide a daily review of activity.