I was recently pointed towards www.reportspammers.net, which is a good resource for all things spam related and is steadily increased the quantity and quality of the information available. As much as I like the statistics that can be gathered from honeypot systems, live and real stats are even better and the data utilised by Report Spammers is taken from the email clusters run by Email Cloud.
One of the first resources released was the global map showing active spam sources (static image below), it is updated hourly and the fully interactive version can be found here.
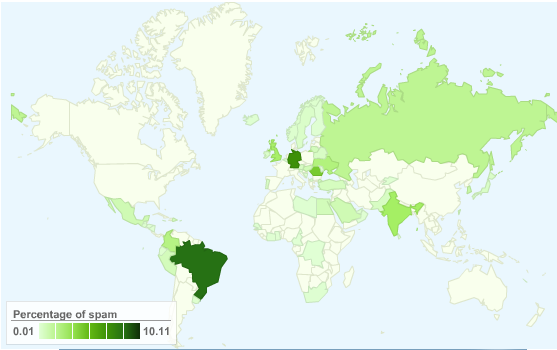
In addition to the global map, Report Spammers also lists the most recent spamvertised sites seen on it’s mail clusters. I’m undecided with the ‘name and shame’ methodoly due to the risk of false postives, but if your looking for examples of spamvertised sites it will prove a good resource (and one I intend to delve deeper into next time I’m bored). Just beware, sites that actively advertise via spam are rarely places that you want to point you home browser at, you have been warned.
If you are wanting a resource to explain spam and the business model behind it Report Spammers could be a good starting point. It even has the ability to explain spam to non-infosec types that still think spam comes in tins. Keep this in mind next time you need to run another information security awareness campaign.
— Andrew Waite
Andy,
Thanks for the info – very useful indeed. Do you have any suggestions for the other types of abuse that comes in – eg 445 port attacks. I noticed dshield.org has something – any recommendations?
Raph
Hi Raph,
Long time. DShield is about the best, can also access the same data via isc.sans.org (which is also an excellent resources for keeping track of ongoing and breaking security news). I’m currently working on building up similar resources from my own systems, but this won’t be ready to go live in the immediate future, but watch this space.
If you are specifically interested in attacks on 445, this is the the ingress point majority of malware captured and monitored by Nepenthes/Dionaea systems, so you can take look at my posts (try this, for example) on the statistics gathered from these systems to get a feel for the frequency of this attack vector.
If you’re looking for different statistics let me know, I may be able to pull some rough and ready data from my existing data sets.
— Andrew