I was recently asked about the network configuration I use for my honeyd sensor. I had thought I’d already written about this so initially went to find the article on honeyd configuration; but my memory was wrong and the original post only covered configuring the guest systems, not the honeyd host itself. So, as I now have a pretty(ish) network diagram showing my setup I may as well correct the earlier omission.
<DISCLAIMER: This may not be the best network design for running honeyd, this is merely how my environment is configured and it works for me as a research platform. As usual, your mileage may vary, especially if your use-case differs from my own>
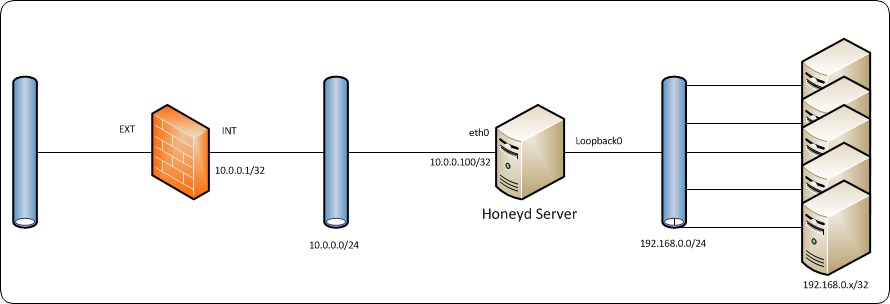
As can be seen, the design has three distinct network segments:
- Publicly route-able IPs
- Internal network for honeypot hosts
- Virtual network for honeyd guest systems. These IP addresses sit on loopback interface on the host, with a static route on the firewall to pass all virtual traffic to the honeyd host.
Using a perimeter firewall with NAT/PAT capabilities allows easy switching between emulated systems and services if your public IP resources are limited; a large network of guests can be configured in advance and left static, then a quick firewall change is all that is required to expose different systems to the world.
Additionally, as much as honeypot systems are designed to be compromised and collect information of malicious attacks (or perhaps more correctly, because of this) , low-interaction systems like honeyd is designed to avoid full compromise. If something goes wrong and the host system gets fully compromised, a (sufficiently configured) perimeter firewall provides some control of outgoing traffic, limiting the attackers options for using the honeypot sensor to attack other systems.
Not much to it really; if you use an different setup and/or can suggest ways to improve the setup let me know, always looking to improve my systems where possible.
— Andrew Waite
hi there (ehm) sir…
I am a college student, and I’ve read and learn a lot about honeypot from this blog and I think it is a great article.
I’d like to ask something about malware if you don’t mind,
right now, I have been running this honeypot system on my campus, and I got only few sample of binaries from the wild. I’ve been running this system for one and a half month, but the result seems quiet disappointing. I was expecting of many of binary sample from this system at first, but it couln’t happen. I used nepenthes honeypot for this system. My system connect directly to the wild (I’m using oublic IP and no local network). What do I do?? do you have solution for this problem??
Also if you don’t mind will you share the binaries that you have collected from your honeypot? I’d like to compare them with mine, and I need them to finish my final project.
Thanks a lot
Sorry for bad english, it’s not my native language.
Hi Mandella,
Glad to here some of my ranting has been useful.
If you’re getting some samples then I’d suggest that everything is working; unfortunately some IP ranges are just less actively targeted than others. If you’re on campus, I’d also suggest contacting your server/network admins to check if additional protection is interfering between the campus perimeter and your host (IPS etc.).
Afraid I don’t share my samples directly ([potential] legal issues etc.) but there are a number of sources that provide the same services Dionaea’s own ore.carnivore.it or the recent project malware.lu are prime examples.
Good luck with your final project.
–Andrew